
Raydium is a Solana-based Automated Market Maker (AMM). Raydium gives users the opportunity to swap and trade, provide liquidity and also to stake and earn the native Raydium token – RAY. Just like other similar platforms, Raydium allows any third-party project to be listed with it. At the time of events TVL on the platform was over $30 million.
On December 16, Raydium announced on Twitter that its platform had been attacked by hackers. There were no details except for the hacker's address.
An exploit on Raydium is being investigated that affected liquidity pools. Details to follow as more is known
— Raydium (@RaydiumProtocol) December 16, 2022
⁰Initial understanding is owner authority was overtaken by attacker, but authority has been halted on AMM & farm programs for now
Attacker accnthttps://t.co/ZnEgL1KSwz
A few minutes before Raydium’s post, the crypto investigator ZachXBT reported that about $2 million stolen from Raydium liquidity pools had already been transferred to ETH. This tweet was a response to the suspicions from swap aggregator PRISM that there was an attack on Raydium.
Then bridged to ETH (~$2m so far)https://t.co/3OYxDThv7I
— ZachXBT (@zachxbt) December 16, 2022
Two days later, Raydium published an analysis of the attack on their liquidity pools.
In short, the hackers gained access to the Pool Owner (Admin) account, and misused the protocols’ fee withdrawal functions to drain the liquidity pools. They had managed to increase the amount of fees too. The attack affected 8 most concentrated out of more than 50 constant product liquidity pools on Raydium. Raydium claimed that all other pools and funds were not affected by the exploit.
Originally reported to be $2 million, the final estimate of the stolen funds was confirmed by Raydium to be $4.4 million. The losses were tracked, and a detailed list of transactions can be accessed here.
The response to the hack included: revocations of the compromised admin account rights and placing a new admin account on a hardware wallet. Also, unnecessary rights were removed or limited on admin accounts
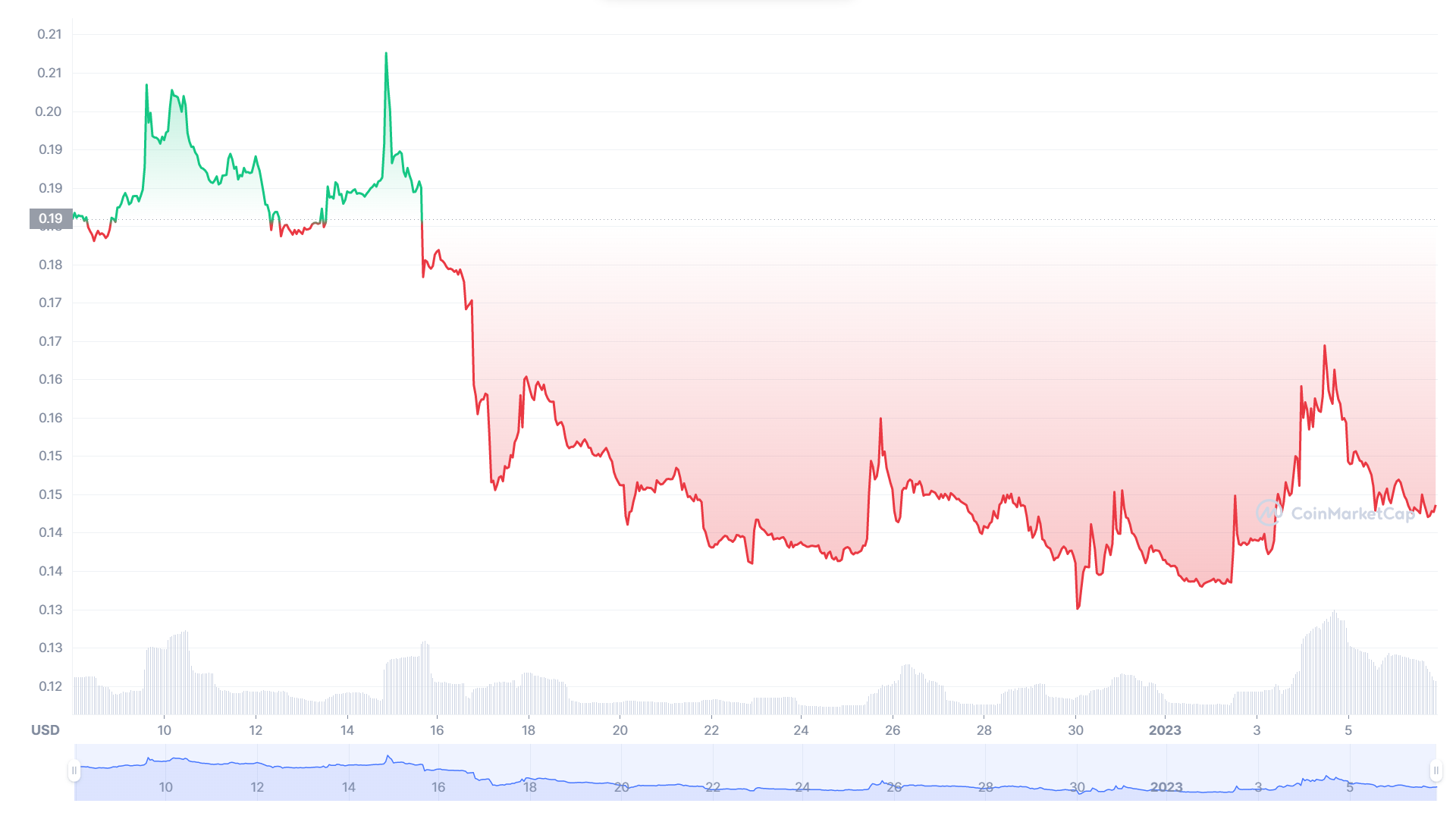
Before the hacker attack, the price of the RAY token fluctuated around $0.19. After the attack, the price dropped to $0.14 and continues to fluctuate at that level.
In the following from Raydium's tweet on December 20, it was not possible to identify the hacker. Raydium also announced an increase in the bug bounty reward.
2/ In an attempt to accelerate recovery, the previous bug bounty has been increased.
— Raydium (@RaydiumProtocol) December 20, 2022
It now includes the entire amount of compromised RAY and a 15% white hat bug bounty of the remaining funds if returned by the attacker.
In the last two weeks, Raydium has been developing a reimbursement plan. For this purpose, a large-scale discussion was held, during which a vote was taken. The vote on two points ended almost unanimously.
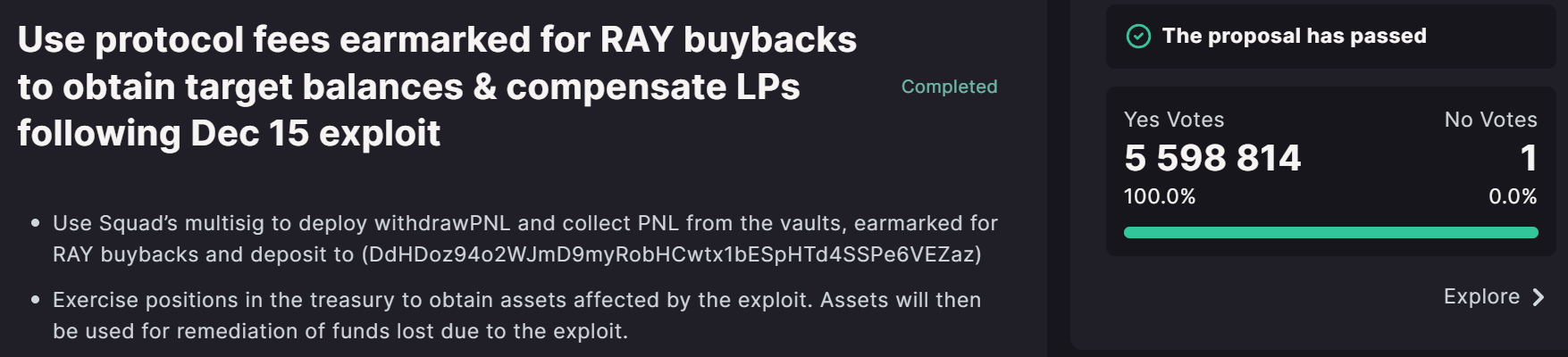
Following this, on January 4, Raydium published a plan to eliminate the consequences of the exploit and the sequence of steps to be taken. The plan consists of two phases. The first phase is now live on the website and will last two months. During the first phase, users who were individual liquidity providers will be able to apply for a refund.
“Following the initial proposal for the remediation of funds, assets in the treasury have been used to obtain the vast majority of assets that were affected during the exploit. The next step is to use the obtained assets to restore losses to users that had liquidity positions in affected pools at the time of the incident.”
And again, another hacker added problems to another crypto company and rode off into the sunset with several million in hand. It is unlikely that this will ever end, so we continue to observe.

